@jenis
2025-10-03T09:51:16.000000Z
字数 6469
阅读 5
Master the KCSA Exam with CertsOut Dumps Questions
未分类
Introduction – Why KCSA Certification Matters
The KCSA certification exam (Kubernetes and Cloud Native Security Associate) is designed for professionals who want to validate their skills in Kubernetes security. With cloud-native adoption growing rapidly, organizations are looking for certified experts to secure their containerized environments. Earning the KCSA IT certification not only boosts your credibility but also opens up exciting opportunities in DevOps and cloud security.
Visit here: https://www.certsout.com/KCSA-test.html
Understanding the KCSA Certification Exam
The KCSA certification exam tests your knowledge of cloud-native security principles, Kubernetes architecture, vulnerability management, and compliance. Many professionals find it challenging to prepare without proper guidance. This is where CertsOut’s real KCSA questions answers make a huge difference by offering targeted and reliable exam prep.
Why Choose CertsOut for KCSA Preparation?
CertsOut specializes in providing real KCSA braindumps that are updated and aligned with the latest exam syllabus. From detailed explanations to KCSA dumps, every resource is designed to ensure your success on the first attempt. With CertsOut, you can save time, reduce stress, and prepare smarter.
Real KCSA Questions Answers for Exam Success
With real KCSA questions answers, you get an authentic exam preparation experience. These materials closely resemble the actual KCSA exam, helping you familiarize yourself with the question patterns and difficulty levels. This builds confidence and increases your chances of passing on your first try.
Flexible Learning with KCSA PDF and Testing Engine
CertsOut provides the KCSA PDF + Testing Engine package for a complete preparation experience. The KCSA PDF allows offline learning, while the CertsOut KCSA Testing Engine simulates the real exam environment. This combination ensures you have both flexibility and hands-on practice.
Benefits of Using Real KCSA Braindumps
Studying with real KCSA braindumps pdf helps you focus on relevant exam topics. Instead of wasting time on unnecessary materials, you’ll concentrate on what really matters. This makes your preparation faster, easier, and more effective.
https://www.certsout.com/Linux-Foundation-Practice-Test.html
Experience the Power of the Kubernetes Testing Engine
The KCSA Exam Testing Tool from CertsOut acts as your personal practice lab. It mimics the real exam environment, tracks your progress, and highlights weak areas. Practicing with the KCSA Testing Engine ensures you’re exam-ready.
Affordable Learning with CertsOut KCSA Dumps
One of the biggest advantages of CertsOut is affordability. With KCSA dumps available at discounted prices, you can access premium exam preparation resources without overspending. It’s an ideal option for candidates who want high-quality study material at a low cost.
How CertsOut Ensures Your Success
CertsOut doesn’t just provide dumps—it ensures your learning journey is smooth and effective. With regular updates, verified content, and practice exams, CertsOut guarantees that its KCSA braindumps remain relevant and reliable. Many professionals trust CertsOut to pass their KCSA certification exam on the first attempt.
Final Thoughts – Advance Your Career with KCSA
The KCSA certification exam is your gateway to excelling in Kubernetes and cloud-native security. With real KCSA practice tests, KCSA PDF + Testing Engine, and updated KCSA braindumps, CertsOut gives you everything you need to succeed. Prepare smartly, save money, and achieve your certification goals confidently.
👉 Get your KCSA dumps from CertsOut today and start your preparation the right way!
FAQs about KCSA Dumps
Q1: Are CertsOut’s real KCSA dumps reliable?
Yes, CertsOut provides updated and verified dumps that reflect the actual exam content.
Q2: Can I use the KCSA PDF for offline study?
Absolutely! The KCSA PDF is perfect for flexible, offline exam preparation.
Q3: How does the KCSA Testing Engine help?
The KCSA Exam Testing Tool simulates the real exam environment, helping you practice effectively.
Q4: Are KCSA braindumps pdf updated regularly?
Yes, CertsOut updates all study materials frequently to match the latest exam pattern.
Q5: What’s the best way to prepare for the KCSA certification exam?
Use the KCSA PDF + Testing Engine combo from CertsOut for a complete learning experience.
Free demo questions:
Question 1
What is Grafana?
AA cloud-native distributed tracing system for monitoring microservices architectures.
BA container orchestration platform for managing and scaling applications.
CA platform for monitoring and visualizing time-series data.
DA cloud-native security tool for scanning and detecting vulnerabilities in Kubernetes clusters.
Reveal Answer Next Question
Question 2
An attacker has successfully overwhelmed the Kubernetes API server in a cluster with a single control plane node by flooding it with requests.
How would implementing a high-availability mode with multiple control plane nodes mitigate this attack?
ABy implementing network segmentation to isolate the API server from the rest of the cluster, preventing the attack from spreading.
BBy distributing the workload across multiple API servers, reducing the load on each server.
CBy increasing the resources allocated to the API server, allowing it to handle a higher volume of requests.
DBy implementing rate limiting and throttling mechanisms on the API server to restrict the number of requests allowed.
Reveal Answer Next Question
Question 3
In a Kubernetes environment, what kind of Admission Controller can modify resource manifests when applied to the Kubernetes API to fix misconfigurations automatically?
AValidatingAdmissionController
BPodSecurityPolicy
CMutatingAdmissionController
DResourceQuota
Reveal Answer Next Question
Question 4
Which of the following snippets from a RoleBinding correctly associates user bob with Role pod-reader ?
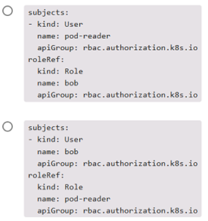
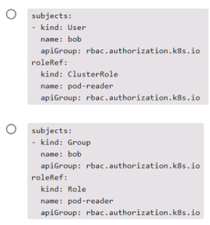
AOption A
BOption B
COption C
DOption D
Reveal Answer Next Question
Question 5
A cluster administrator wants to enforce the use of a different container runtime depending on the application a workload belongs to.
ABy manually modifying the container runtime for each workload after it has been created.
BBy modifying the kube-apiserver configuration file to specify the desired container runtime for each application.
CBy configuring a validating admission controller webhook that verifies the container runtime based on the application label and rejects requests that do not comply.
DBy configuring a mutating admission controller webhook that intercepts new workload creation requests and modifies the container runtime based on the application label.
Reveal Answer Next Question
Question 6
Why might NetworkPolicy resources have no effect in a Kubernetes cluster?
ANetworkPolicy resources are only enforced if the Kubernetes scheduler supports them.
BNetworkPolicy resources are only enforced if the networking plugin supports them.
CNetworkPolicy resources are only enforced for unprivileged Pods.
DNetworkPolicy resources are only enforced if the user has the right RBAC permissions.
Reveal Answer Next Question
Question 7
What is the purpose of an egress NetworkPolicy?
ATo control the incoming network traffic to a Kubernetes cluster.
BTo control the outbound network traffic from a Kubernetes cluster.
CTo secure the Kubernetes cluster against unauthorized access.
DTo control the outgoing network traffic from one or more Kubernetes Pods.
